Google Chrome is my favorite browser and with the latest update in Chrome Beta it has again gained much of my attention. Chrome Beta has many new features which includes noisy tab tracking, improved malware detection and a new look on Windows 8 "Metro" mode. Chrome Dev team is working very hard in improving the overall experience of your browsing. Notice your Chrome Beta carefully to get familiar with these useful tools.
Showing posts with label Security Awareness. Show all posts
Showing posts with label Security Awareness. Show all posts
January 21, 2014
Google Chrome update : Brings noisy tab tracking, enhanced malware detection and much more
Posted by
Kanwaljeet Singh

#Tech Discussion
Read full article -->
#Comment
Google Chrome is my favorite browser and with the latest update in Chrome Beta it has again gained much of my attention. Chrome Beta has many new features which includes noisy tab tracking, improved malware detection and a new look on Windows 8 "Metro" mode. Chrome Dev team is working very hard in improving the overall experience of your browsing. Notice your Chrome Beta carefully to get familiar with these useful tools.
Labels: App News, chrome, Google, Security Awareness, Tech NEWS
January 01, 2014
Ransomware the biggest Threat
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment
Ransomware is a kind of malware that restrict you from accessing your computer untill you pay money to attacker and take up all accessing rights from you and demands for money (ie. ransom) to get back your all data. It basically encrypt your data and even you are able to open your files , they are not readable and attacker has only one intention that he/she demands for money and doesn't decrypt your data untill you pay ransom.
Labels: security, Security Awareness, threat
December 29, 2013
Software to Hardware : NSA intercepted computer deliveries to enter into your system
Posted by
Kanwaljeet Singh

#Tech Discussion
Read full article -->
#Comment
It all began with the news of NSA being hacking computers across the globe to fulfill whatever their aims were. But now according to a stunning report by German magazine, NSA has intercepted the computer deliveries to install or exploit hardware into them and later use it for accessing those machines easily. Moreover they even hijacked Microsoft's bug report system to do better spy o n their targets.
December 28, 2013
Guardian app from CreativeThoughts on Windows Phone 8 is designed to increase women security in India
Posted by
Kanwaljeet Singh

#Tech Discussion
Read full article -->
#Comment
 |
| Guardian app on Windows Phone 8 (From CreativeThoughts) |
Tracking is also one of the very useful measures at times. This security application on your Windows Phone 8 tracks your every movement and let your friends and family follow your every movement using Microsoft Bing Maps and Windows Azure Cloud service.
Labels: App News, microsoft, Security Awareness, Windows Phone 8
December 10, 2013
Much enhanced security features to be added for all Microsoft accounts - Microsoft
Posted by
Kanwaljeet Singh

#Tech Discussion
Read full article -->
#Comment
Internet widespread is happening at much greater pace than our Galaxy is expanding. More the internet widespread, more number of threats (Official and Unofficial) originates from different parts of the Digital world through different means. Microsoft has finally decided to fight back strongly with all the odds of the digital world. They are planning to bring more enhanced security features to all Microsoft accounts across the globe which will cover around 700 million people. In past they added Two-Step verification method for all of their users and for the future they will bring Recent Activity, Recovery Codes and Better Security Notifications.
Labels: microsoft, Security Awareness, Tech NEWS
November 18, 2013
Google and Microsoft to take the lead for stopping child pornography
Posted by
Kanwaljeet Singh

#Tech Discussion
Read full article -->
#Comment
Internet is slowly but surely eating us in many ways. The most sensitive part of our society, childs, are more prone to it if proper restrictions are not imposed on some of the online content. In this regard Microsoft and Google has taken the lead by which they are making harder for users to find most of the illegal images online. When combined, both search giants makes the 95% of the total search queries of the world.
Labels: Digital Inspiration, Google, Internet, microsoft, Security Awareness
October 11, 2013
How to create a password reset disk
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment
Password Reset disk is a kind of personal storage device that contain the password key which you can use for resetting your password details whenever you have forgotten. It is very helpful as it allows access to your stuffs in your computer in such situation. Once you create a password disk ,you can get access to your computer even if you forget your password. Password reset disk will help you to reset your password and one more interesting thing ,you don't need to create it again and again and doesn't matter how many times you have changed your password. You can use any hardrive , pen-drive or any other storage to create a password reset disk.
Labels: How to's, password reset disk, reset disk, Security Awareness
October 01, 2013
Guidelines for safe online banking
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment
Online banking also known as Net-banking is a practice of doing things on internet like bank transactions , paying bills and withdrawing of money .In modern lifestyle ,everyone wants to complete work in seconds and online banking let you to do any transaction from home with having to go anywhere and saves a lot of time.Online banking is really helpful as customer need not to wait for bank statements ,they can easily access their accounts and check their balance anytime just by logging in. They can catch unusual activity or any kind of discrepancy. But you know every technology has its pros and cons. You have to be very careful while using net-banking.
Labels: online banking, Security Awareness
August 31, 2013
Information Security
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment
Information Security is the defending your information from unauthorize access or measures taken to protect data from going into wrong hands. In today's computerised world we are mostly used to with information through PC's ,laptops and many other mobile devices and to our comfort we usually store our info (including credentials) in our personal devices.This cause an ease to access our info anywhere but in parallel there are also some security threats to our personal data, there is a substantial need to secure our data from theft or unauthorize access.
August 26, 2013
Malware :How to get rid of it.
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment
Malware is a malicious software that is designed to penetrate into a computer system or get access to a computer and restricting the computer's normal operation without owner's permission. Malware can be in the form of a viruses,trojan horse,worms ,rootkits and spywares and most of the malwares are designed to steal your confidential informaton from your computer.They can intrude into unprotected computers in the form of e-mail attachments.Here are some of the forms of malwares that you need to know and tips to get protected from such malwares.
Labels: How to's, malware, Security Awareness, Tips & Tricks
August 13, 2013
August 07, 2013
E-mail Security
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment

We all are very familiar to e-mails ,and generally internet users are very much familiar to the e-mails.E-mails are just like the post cards and contain the information to whom they are proposed so they are meant to kept private and personal email ids should not be shared with anyone. Sharing involves a lot of risk and when it comes to security , you have to be very updated with security tactics provided to you by e-mail service provider.
Labels: email security, security, Security Awareness, Tips & Tricks
August 02, 2013
Downloading risks
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment

Downloading process includes accessing of remote files or programs that can be viewed on personal computer with the help of an internet.
We download a lot of files like media files, docs and pdfs etc. as these are present on remote computers which are shared by different people.Opening pictures and e-mails link that direct on a website ,copying word files and pdfs from company's network as well as upgrading software from web and transferring music files from a computer are a part of downloading. Downloading files from internet may include installation of some kind of programs.Opening a picture media files,links and downloading a music files may not be same as they represent,but these contents may also have some involvement of malicious softwares like viruses,worms and many destructive programs.
Labels: downloading, downloading risks, risks, Security Awareness
August 01, 2013
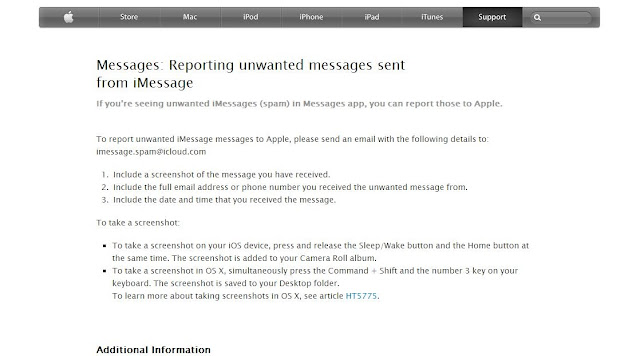
Got a SPAM Message? Report it to Apple
Posted by
Kanwaljeet Singh

#Tech Discussion
Read full article -->
#Comment
Labels: Apple Inc., Security Awareness, SPAM, Tech NEWS
July 28, 2013
ATM Threat:Some tips and guidelines
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment

ATM (Automated Teller Machine) came into existence in 1960.It's basic aim was the provision of cash for its customers wherever required from nearest ATM.It proved out to be the best technological development as it helps all the financial institutions to provide 24 X 7 services for their customers and also provide the convenience for the customers to get cash wherever they are in need.
Labels: ATM, Security Awareness, threat, Tips & Tricks
July 26, 2013
Android under attack
Posted by
Arun

#Tech Discussion
Read full article -->
#Comment

Attackers have now set their target on android OS and they are exploiting the android vulnerability due to which attacker can easily creep into a user's phone without changing the digital signature of that app.This could get them control remotely over victim's phones that can lead to sending SMS, disabling the security of phone and stealing of data.Till now six apps of android have been detected as hijacked.
Labels: Android, android attack, Hacking, Security Awareness, Tech NEWS
July 24, 2013
Browser Security
Posted by
Kanwaljeet Singh

#Tech Discussion
Read full article -->
#Comment
 We are so concern about the security and if it is about ourself ,our resources ,our data or any our stuff .Browser is a software tool that runs on internet and we use to get information from web. It displays the web pages.It's main purpose is to bring requested information by a client from server. It is used on PC's as well as on mobile phones to get access to information.There are different technologies that support web browsers like java, frames, xhtml, jsp and many more, all these technologies have made easier to use internet.
We are so concern about the security and if it is about ourself ,our resources ,our data or any our stuff .Browser is a software tool that runs on internet and we use to get information from web. It displays the web pages.It's main purpose is to bring requested information by a client from server. It is used on PC's as well as on mobile phones to get access to information.There are different technologies that support web browsers like java, frames, xhtml, jsp and many more, all these technologies have made easier to use internet.Labels: Internet, Security Awareness
July 22, 2013
Internet Ethics
Posted by
Kanwaljeet Singh

#Tech Discussion
Read full article -->
#Comment
Ethics are the set of rules that tells the acceptable behaviour of an individual while using the internet.One of the common issue of internet ethics is violation of copyrights.Creating duplicates of copyright content without approval of authors and accessing personal information of others without knowing them are against the internet ethics.Internet ethics differentiate between what is right and wrong and it respect the rights and property of others on internet.
Labels: Ethics, Internet, Security Awareness
Subscribe to:
Comments (Atom)